Understanding the Challenges of Asymmetric Warfare in the 21st Century
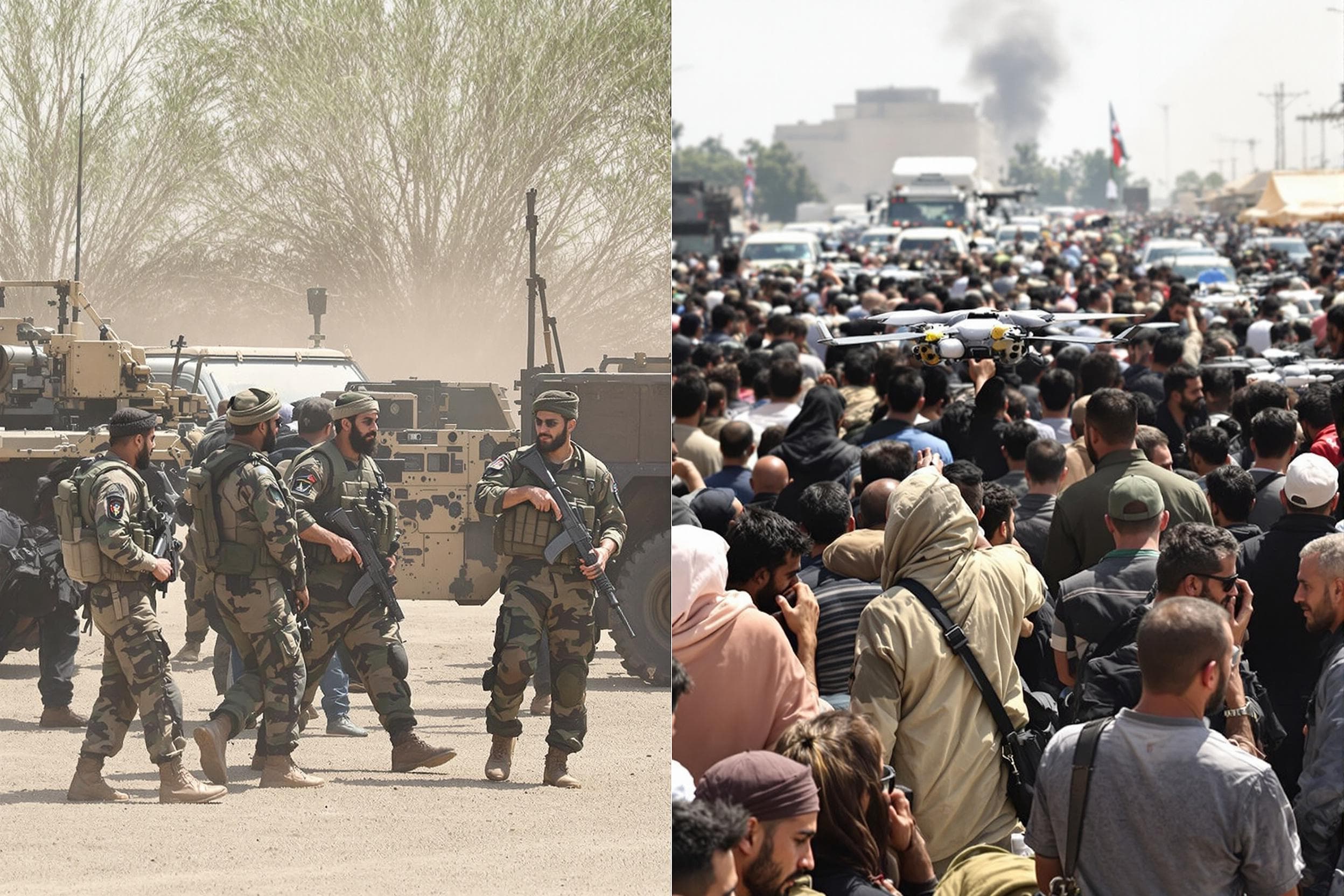

Introduction: The Enduring Reality of Asymmetric Conflict
For those who have served in the post-9/11 era, the term "asymmetric warfare" is more than just doctrine – it's lived experience. It describes conflicts fought between belligerents whose relative military power, strategies, and tactics differ significantly. Typically, this involves conventional state militaries facing non-state actors, insurgents, or terrorist groups who lack comparable firepower but leverage unconventional methods to exploit vulnerabilities.
While the concept isn't new, the dynamics of asymmetric warfare in the 21st century present unique and evolving challenges, profoundly shaping operational planning, force protection strategies, and the technological requirements for modern armed forces. Understanding these challenges is the first step toward developing effective countermeasures and ensuring mission success while safeguarding personnel.
Key Challenges Defining Modern Asymmetric Warfare:
-
The Blurred Lines: Identifying Combatants vs. Non-Combatants
- The Challenge: Perhaps the most persistent difficulty is distinguishing legitimate threats from the civilian population amongst whom adversaries often embed themselves. Fighters may not wear uniforms, blend seamlessly into daily life, and use civilian infrastructure for cover and operations. This ambiguity complicates targeting, increases the risk of civilian casualties (which adversaries often seek to provoke for propaganda value), and puts immense pressure on soldiers' judgment under duress.
- Impact: Strict Rules of Engagement (ROE) designed to protect civilians can sometimes be exploited by adversaries, creating tactical dilemmas. Intelligence gathering becomes paramount but is often difficult in denied or culturally complex areas.
- Fact: Operations in dense urban warfare environments, common in places like Iraq and Afghanistan, epitomize this challenge, where the "three-block war" requires simultaneous combat, stabilization, and humanitarian support within the same small area.
-
Democratization of Technology: Leveling the Playing Field (Partially)
- The Challenge: While conventional forces maintain technological superiority in high-end systems, adversaries increasingly leverage readily available, commercial-off-the-shelf (COTS) technology for significant effect. This includes encrypted communication apps, commercially available drones/UAVs for reconnaissance and attack, GPS devices, readily accessible bomb-making instructions online, and sophisticated use of the internet for recruitment and propaganda.
- Impact: This erodes some traditional advantages. Small, cheap drones can conduct ISR previously requiring expensive assets. Secure comms make SIGINT harder. Online networks facilitate global reach for local groups.
- Fact: The use of modified commercial drones by groups like ISIS for surveillance and dropping small munitions demonstrated the rapid adoption and adaptation of accessible technology by non-state actors, forcing rapid development of Counter-UAS (C-UAS) systems.
-
Information Warfare and Narrative Control:
- The Challenge: Asymmetric adversaries often prioritize the information domain, recognizing they cannot win purely kinetic engagements. They use propaganda, disinformation, and manipulation of social and traditional media to sow dissent, erode public support (both domestic and international) for the conventional force's mission, recruit members, and create an atmosphere of fear or legitimacy for their cause.
- Impact: Military actions are scrutinized globally in near real-time. Unfavorable narratives, even if inaccurate, can have strategic consequences, impacting political will and coalition cohesion. Winning the "battle of the narrative" is often as crucial as winning tactical engagements.
- Fact: The speed and reach of social media allow adversaries to disseminate their version of events instantly, often bypassing traditional media filters and directly influencing target audiences worldwide.
-
Exploitation of Rules and Law:
- The Challenge: Conventional forces operate under strict ROE and the Law of Armed Conflict (LOAC), designed to minimize suffering and maintain ethical standards. Asymmetric adversaries frequently operate outside these constraints, deliberately using tactics like human shields, feigning surrender, attacking protected sites (hospitals, mosques), or using civilian infrastructure militarily, knowing the conventional force's response is constrained.
- Impact: This creates tactical disadvantages and ethical dilemmas. Adherence to rules can seem like weakness to an adversary who flouts them, while any perceived violation by conventional forces is heavily publicized and exploited.
- Fact: Documented instances of adversaries using hospitals or schools as command centers or firing positions force agonizing decisions on conventional commanders bound by LOAC.
-
Protracted Conflicts and Resource Drain:
- The Challenge: Asymmetric strategies often focus on longevity over decisive victory. By avoiding direct confrontation and employing hit-and-run tactics, IEDs, and political destabilization, they aim to inflict casualties incrementally, disrupt governance, and erode the political will of the stronger power and its populace through a prolonged, costly engagement.
- Impact: These conflicts test national endurance, consuming vast resources (financial, human, political) over years or decades. Maintaining operational tempo, force morale, and public support becomes a significant strategic challenge.
- Fact: The length and cost of counter-insurgency (COIN) campaigns in recent decades highlight the effectiveness of protracted warfare strategies employed by asymmetric opponents.
Adapting Through Technology: Enhancing Resilience and Awareness
While these challenges are formidable, technology plays a critical role in mitigating risks and enhancing effectiveness in asymmetric environments:
- Advanced ISR: Persistent surveillance from various platforms helps differentiate threats, monitor patterns of life, and provide early warning.
- Data Fusion & AI: Processing vast amounts of intelligence data can identify subtle threat indicators and networks that human analysis might miss. AI sound recognition can help pinpoint weapon fire origins even in chaotic urban soundscapes.
- Secure Communications: Resilient, encrypted comms are vital for coordination and disseminating threat warnings rapidly.
- Enhanced Force Protection: Advanced armor, C-UAS systems, and counter-IED technologies directly address specific asymmetric tactics.
- Blue Force Tracking (BFT): In fluid, complex environments where friendly units can be dispersed and lines blurred, knowing the precise, real-time location of every soldier is fundamental. Wearable BFT systems, like those developed by Unbound Autonomy, provide critical situational awareness, reduce fratricide risk, enable better command and control (C2), and ensure personnel accountability – all essential elements for navigating the ambiguities of asymmetric warfare. Knowing where your people are is the first step to protecting them.
Conclusion: Preparedness Through Understanding
Asymmetric warfare remains a dominant feature of the global security landscape. Its challenges – ambiguous enemies, leveraging accessible tech, information battles, exploiting legal frameworks, and protracted engagements – demand continuous adaptation from modern militaries. Understanding the nuances of this environment is crucial for developing effective TTPs, training programs, and technological solutions.
By investing in technologies that enhance situational awareness, improve intelligence gathering, secure communications, and provide robust force protection, including reliable Blue Force Tracking and soldier status monitoring via advanced wearable devices, we equip our forces to operate more safely and effectively against the complex threats of the 21st-century asymmetric battlefield. Readiness begins with acknowledging the true nature of the fight.