Technology's Role in Enhancing Force Protection Strategies: Safeguarding Our Most Valuable Asset

Introduction: The Imperative of Force Protection
Force Protection (FP) isn't just a doctrinal term; it's a fundamental responsibility of command and a critical enabler of mission success. At its core, FP encompasses all measures taken to prevent or mitigate hostile actions against personnel, resources, facilities, and critical information. In today's increasingly complex and lethal operating environments, characterized by asymmetric threats, hybrid warfare, and the resurgence of peer and near-peer competition, robust FP strategies are more crucial than ever.
While sound tactics, techniques, procedures (TTPs), and leadership remain foundational, technology has emerged as a decisive force multiplier in our ability to protect our warfighters. Leveraging cutting-edge advancements allows us to anticipate threats, enhance situational awareness, speed up response times, and ultimately, improve soldier survivability.
The Evolving Threat Landscape Demands Technological Adaptation
Gone are the days of clearly defined front lines. Modern threats are often dispersed, technologically sophisticated (even for non-state actors), and adept at exploiting vulnerabilities. From improvised explosive devices (IEDs) and sophisticated ambushes to drone swarms, cyber-attacks, and electronic warfare (EW) jamming, the challenges are multifaceted. Relying solely on traditional FP measures is no longer sufficient. Technology provides the tools to stay ahead of adversaries operating across multiple domains.
Key Technological Pillars Strengthening Force Protection:
-
Intelligence, Surveillance, and Reconnaissance (ISR) Platforms:
- What it is: Unmanned Aerial Vehicles (UAVs/drones) of various sizes, ground-based sensors (acoustic, seismic, thermal), satellite imagery, signals intelligence (SIGINT).
- FP Impact: Provides persistent surveillance over areas of interest, enabling early warning of enemy movement, potential ambush sites, or IED emplacement activities. High-resolution imagery and sensor data allow for detailed threat assessment before troops are committed or exposed. Technologies like Ground Penetrating Radar (GPR) integrated into route clearance packages directly detect subsurface threats.
- Fact: The proliferation of small, affordable drones means ISR capabilities, once the domain of strategic assets, are increasingly available at the tactical level, drastically improving unit-level FP.
-
Blue Force Tracking (BFT) and Wearable Technology:
- What it is: Systems providing real-time location data of friendly forces, often integrated with communication and status reporting capabilities via wearable devices.
- FP Impact: This is fundamental. Knowing the precise location of every soldier drastically reduces the risk of fratricide (friendly fire incidents), a tragic but persistent danger in complex operations. BFT enhances command and control (C2), allowing leaders to maneuver forces safely, coordinate fire support accurately, and maintain personnel accountability during chaotic engagements. Modern wearable technology, like that developed by Unbound Autonomy, goes beyond simple location, potentially integrating health monitoring (soldier status) and environmental sensors, adding layers to individual protection.
- Fact: Studies following operations in Iraq and Afghanistan consistently highlighted BFT as a critical factor in reducing fratricide and improving small unit coordination and safety.
-
Artificial Intelligence (AI) and Data Fusion:
- What it is: Using machine learning algorithms to analyze vast amounts of data from disparate sources (ISR feeds, BFT, SIGINT, logistics data, open-source intelligence).
- FP Impact: AI excels at identifying subtle patterns and anomalies invisible to human analysts. It can predict likely threat locations, detect deviations from normal activity patterns that might indicate hostile intent, automate threat recognition in sensor feeds (like AI sound recognition for weapon types or direction), and fuse sensor data to create a more accurate Common Operating Picture (COP). This accelerates the OODA loop (Observe, Orient, Decide, Act) for FP decision-making.
- Fact: AI-powered predictive analytics are being explored by DARPA and other defense research agencies to forecast potential IED locations or ambush spots based on historical data and terrain analysis with increasing accuracy.
-
Secure and Resilient Communications:
- What it is: Encrypted radios, satellite communications (SATCOM), mesh networks, tactical data links resistant to jamming and interception.
- FP Impact: Reliable communication is the bedrock of coordinated action. Secure comms ensure that threat warnings, BFT data, and C2 instructions are passed quickly and accurately without compromise. Network resilience ensures that communication pathways remain open even when under electronic attack, preventing units from becoming isolated and vulnerable.
- Fact: Advances in anti-jamming techniques and Low Probability of Intercept/Low Probability of Detection (LPI/LPD) waveforms are crucial for maintaining communication superiority, a key enabler for FP in contested EW environments.
-
Counter-Threat Technologies (C-UAS, EW, Physical Protection):
- What it is: Systems designed to directly neutralize threats – Counter-UAS systems (detection, tracking, jamming, kinetic kill), Electronic Warfare suites (jamming enemy comms/drones), advanced body armor, vehicle protection systems, and access control technologies.
- FP Impact: Provides direct defense against specific threats. C-UAS systems protect personnel and facilities from weaponized or surveillance drones. EW can disrupt enemy command and control or remotely detonated devices. Advanced materials improve individual and vehicle survivability against ballistic threats and blasts.
- Fact: The rapid evolution of C-UAS technology reflects the immediate and widespread threat posed by drones, demonstrating how technology directly counters emerging dangers to force protection.
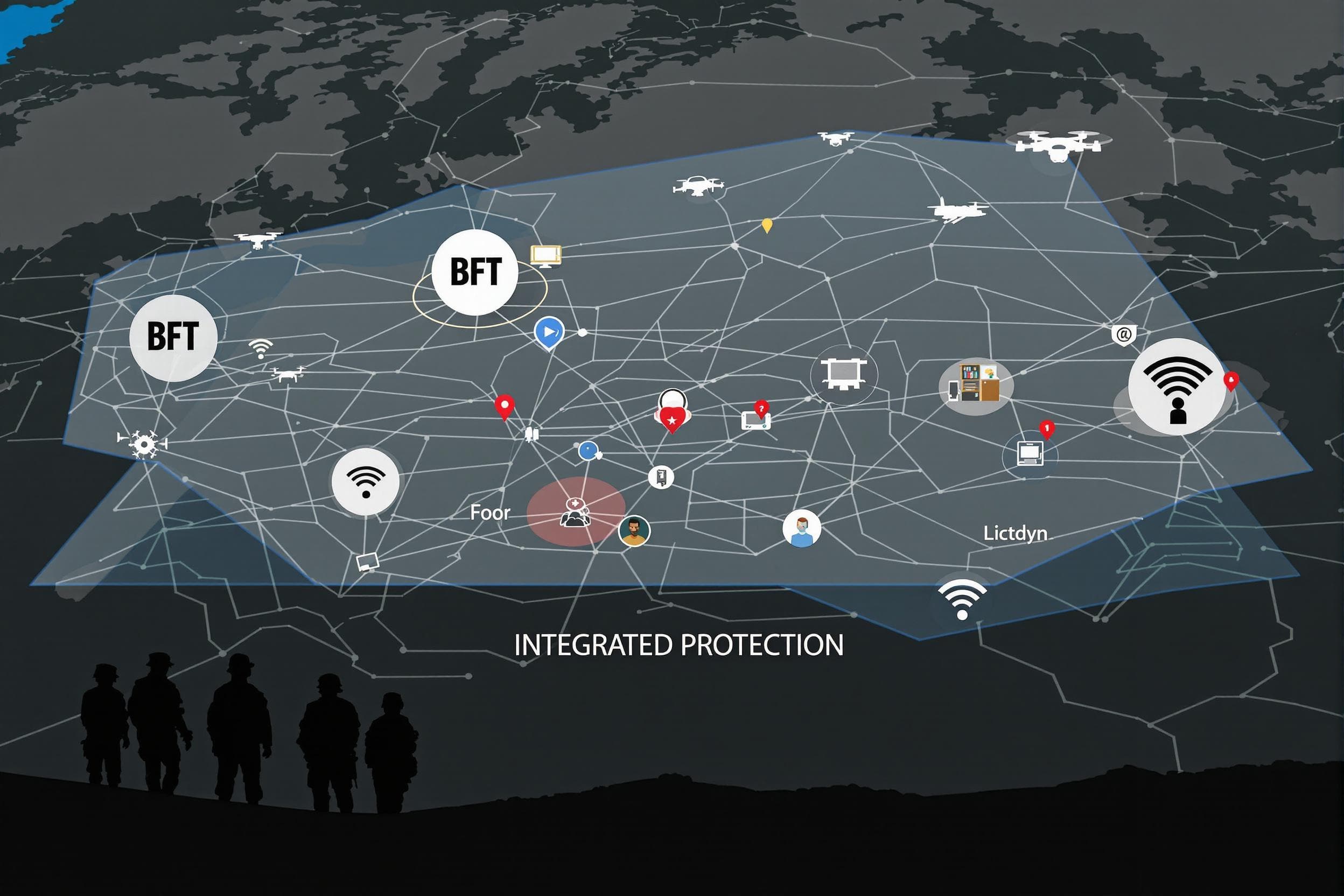
The Synergy of Integration: Unbound Autonomy's Vision
The true power of these technologies lies not in isolation, but in their integration. Imagine an ISR drone detecting suspicious activity. AI analyzes the feed, cross-references it with historical data, and flags a potential IED threat. This alert is instantly pushed via secure comms to nearby units, whose positions are precisely known via Unbound Autonomy's wearable BFT system. Commanders, viewing the integrated COP, can reroute patrols, dispatch EOD, or task other assets, all while maintaining real-time awareness of their soldiers' locations and status.
This seamless flow of information, enabled by integrated technologies, transforms FP from a reactive posture to a proactive, data-driven strategy. At Unbound Autonomy, our focus on reliable, rugged wearable BFT solutions provides the foundational layer of individual soldier location and status – critical data points that feed into this larger, technologically enhanced force protection ecosystem.
Conclusion: Investing in Technology is Investing in Our People
Technology is not a replacement for sound judgment, rigorous training, or courageous leadership. However, it is an indispensable tool that significantly enhances our ability to implement effective force protection strategies. By embracing advancements in ISR, BFT, AI, communications, and counter-threat systems, we provide our soldiers with the awareness, information, and protection they need to operate and succeed in demanding environments.
At Unbound Autonomy, we are committed to developing and deploying technology, particularly in wearable blue force tracking and soldier status monitoring, that directly contributes to safeguarding our most valuable asset – the men and women who serve. Enhancing force protection through technological superiority isn't just an advantage; it's an obligation.